Playing With S3 Part 2
S3 Bucket Enumeration Via Response
Hi Hackers,
In this article, I will be talking about one of my recent find on a program triaged as critical.Target "redacted.com" was a large scope and was using amazon web services.
You can find previous article on s3 bucket enumeration here
After enumerating subdomains using subfinder, I randomly visited all subdomains and my burpsuite was running in background. After sometime i just visited my burpsuite's HTTP history tab where i can list of all of the requests that i have made and the responses received.
Here i went to BURP tab > search and searched keyword
"amazonaws.com"
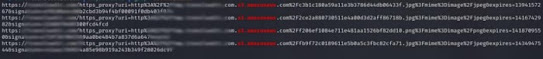
Here you can see one of the s3 bucket using by redacted.com was leaking in response.
Just copied this URL and paste it in browser.
Eg: http://bucket.
The s3 bucket was Open to public and was leaking user attachments, bills, identity cards, etc..
Now i need to check for another privileges like uploading a file / removing a file.
But access was denied.
So i directly reported to the company
Triaged as critical.
Rewarded $$$$$ INR. (Indian rupees).
Follow me on twitter: https://twitter.com/r0074g3n7
You Can Buy Me A Coffee via : https://www.buymeacoffee.com/error4004



P1 boom! Nice Work
ReplyDelete