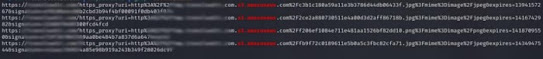
Hunting on memcached servers: Dumping data

What is a Memcached server? Memcached servers are used to store and retrieve data in the form of key-value pairs. When client requests for data from server, its checks for the data stored in the cache. If the data is available, it is loaded into the memory. If the data is not present, the server fetches it from the backend storage and stores it in its cache for future requests. So, it is used to speedup the web application by reducing the database load. LETS DISCUSS! Today we will be discussing on my recent bounty i got for key dumping from an open memcached server. I got an ip from censys search which is targets ip. So as an initial recon i used nmap for scanning the ip. nmap IPADDRESS -Pn from initial scan i was able to find a port 11211 which is Memcached!! So i started pentesting on the server to retrieve data if it has no authentication. For confirmation i tried to connect the Memcached server via Telnet. telnet IPADDRESS 11211 Wow! I was able to connect to the server without a...